Network security operations (SecOps)
Security breaches are frequently caused by security procedures that are there on paper but don’t get properly followed through on. The procedures are usually good, but the everyday execution can be lacking. DataMiner provides you with a broad range of tools to assist your SecOps teams with keeping your network secure, automating these procedures in operational flows, ensuring consistent execution and thus reducing risks. On top of that, DataMiner provides you with a full set of metrics, allowing you to intelligently keep track of risks as well as unusual behavior on your network.
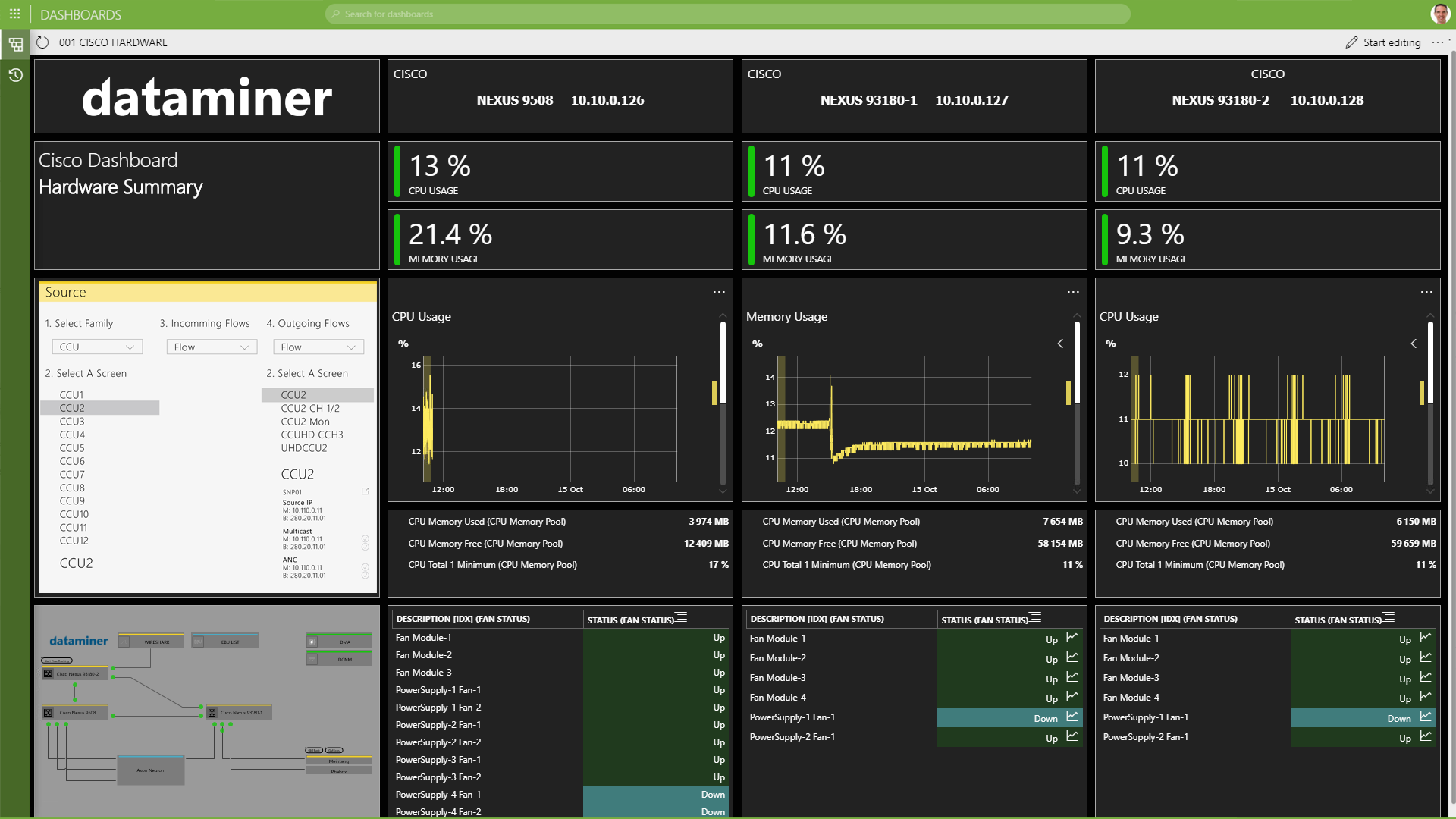
- DataMiner supports the integration of all types of security infrastructure, be it physical (badges, cameras, etc.), network probes, or software.
- By orchestrating your full stack from physical infrastructure up to the service level, DataMiner will keep your network safe, automating all security procedures, including whitelisting/blacklisting ACLs on your switches, updating software versions and configurations to the latest golden standard, and more.
- Since DataMiner is aware of your infrastructure on the service level, access control and detection of unwanted activity can happen in an intelligent way. DataMiner can update ACLs every time a new service is set up, adding the hosts on the fly, and also remove access rights again when a service ends.
- Integrating with every level of your infrastructure, DataMiner can even automatically turn off unused network ports dynamically, using information about top-level services. This is because DataMiner is a full-stack service orchestration solution, enabling finer grained security policies aligned with network orchestration.
- With DataMiner synthetic testing, automatic tests can be executed, for example testing for standard passwords being enabled on new devices, or testing configurations after each maintenance cycle.
- DataMiner provides you with an AI engine with a full stack of metrics. This means that DataMiner monitoring provides an intelligent view on streams in the network, so that your operators get alarm notifications when necessary.
- With a rich set of metrics and KPIs that can be used by the DataMiner AI engine, it is possible to automatically signal abnormal conditions. Full stack monitoring allows you to for example monitor the stack requests on a VOD server and align this with the service layers to automatically signal whether an activity constitutes a possible attack.
- With DataMiner anomaly detection, operators can be warned about abnormal behavior when certain trends change, indicating a possible security breach.
- DataMiner cloud connectivity allows you to securely access your monitoring systems from anywhere.
Associated Markets:
Service ProvidersService Providers - Cloud
Service Providers - Cloud - Broadband
Service Providers - Cloud - IoT
Service Providers - Satellite
Service Providers - Satellite - O&G (Energy, Oil, Gas)
Service Providers - Satellite - Mobility (Mobile, Land, Airborne & Maritime)
Service Providers - Network
Service Providers - Network - Media
Service Providers - Network - Data
Service Providers - Network - ICT
Service Providers - Broadband
Service Providers - Broadband - WiFi
Government & Defense
Government & Defense - Border Security
Government & Defense - Fixed & Mobile Com.
Government & Defense - Disaster Recovery