This article kicks off a new series about security. And more specifically, about how you can make sure your DataMiner system is configured as securely as possible.
Let’s start by stating the obvious: it is recommended to keep your system up to date and to run the most recent version of the chosen release track. Any improvements for known vulnerabilities and any new security-related features are always available in the latest version.
For more information about the most recent version, see DataMiner Software downloads.
In this first post, we’ll talk about securing client-server communication in your DataMiner system.
Cube/external clients
Encryption
Communication between DataMiner and any client application is encrypted by default since DataMiner 10.1.7.0. On lower versions, it is recommended to enable the ‘RequireEncryptedConnections‘ setting. This can be done by adding the following tag to the MaintenanceSettings.xml:
<RequireEncryptedConnections>TRUE</RequireEncryptedConnections>
Communication is encrypted by the Rijndael algorithm using a 256-bit key, which is negotiated over a 1024-bit RSA encrypted communication channel.
For more information, see Encrypted Connections.
Web Services
From 10.0.11 and 10.0.0 (CU6) onwards, Web Service connections are considered insecure and deprecated. In older versions, it is recommended to use Remoting instead. This can be configured in the connection settings on the login page.
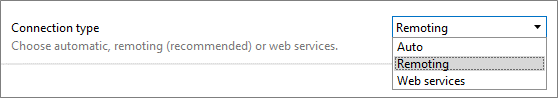
Connection Settings/Endpoints
When the ‘RequireEncryptedConnections’ setting is enabled, it is recommended to make sure clients connect over Remoting, making their connection encrypted. To ensure clients automatically use Remoting, verify the following line contains ‘type=RemotingConnection’ in your ConnectionSettings.txt. This is also an opportune time to revise any exceptions added to this file.
This file is located in C:\Skyline DataMiner\Webpages\ConnectionSettings.txt
* type=RemotingConnection;polling=0;zip=true
When SLNet is running on port 8004 (the default port) and you have disabled Webservices (or use a DataMiner version higher than 10.0.11.0-CU0), you can also block requests to Endpoints.txt. This prevents exposing unnecessary information about the services on your Web Server to potential attackers.
To do this, add an Application Request Filtering Rule that denies requests to Endpoints.txt.
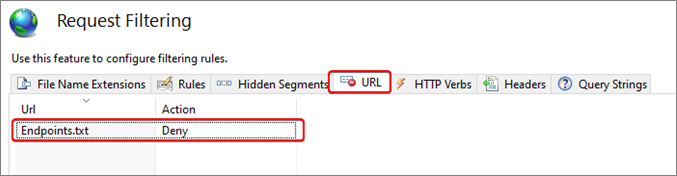
Web Applications
By default, web applications connect to DataMiner over HTTP (80) or HTTPS (443). HTTP is unencrypted and vulnerable to man-in-the-middle attacks. HTTPS mitigates this by using TLS (Transport Layer Security) to encrypt the HTTP traffic.
It is recommended to block all HTTP requests in IIS and redirect all HTTP requests to the HTTPS binding. Follow these steps to enable HTTPS on your DataMiner system. It is recommended to use certificates issued by a trusted Certificate Authority (CA). TLS is considered the upgraded version of SSL (Secure Sockets Layer). In the following matrix, any version of SSL/TLS older than 1.2 is deprecated and thus insecure.
| Protocol | Published | Status |
| SSL 1.0 | Unpublished | N/A |
| SSL 2.0 | 1995 | Deprecated since 2011 |
| SSL 3.0 | 1996 | Deprecated since 2015 |
| TLS 1.0 | 1999 | Deprecated since 2020 |
| TLS 1.1 | 2006 | Deprecated since 2020 |
| TLS 1.2 | 2008 | Supported |
| TLS 1.3 | 2018 | Supported (most secure) |
At the time of writing, all major browsers support TLS 1.2, and most of them already support TLS 1.3. Therefore, we recommend disabling all versions of SSL and TLS 1.0/1.1. On systems where all clients support TLS 1.3, it is possible to disable TLS 1.2 as well.
For more information on how to disable SSL/TLS, see:
- Disabling SSL 2.0 by default
- Disabling SSL 3.0 by default
- Disabling TLS 1.0 by default
- Disabling TLS 1.1 by default
- Disabling TLS 1.2 by default
In our next article about the firewall, we will show you how to harden your servers hosting DataMiner.
wow, that’s a great article!
There’s a link at the bottom of the Disabling SSL/TLS pages that has a quick and easy PowerShell script, that will disable all bar TLS 1.2, which you can also be easily modify to disable all bar TLS 1.3.
https://docs.microsoft.com/en-us/troubleshoot/windows-server/identity/disable-tls-1-1dot1-mbam-servers
You might want to look at the ciphers, hashes and key exchange algorithms used as well, https://docs.microsoft.com/en-US/troubleshoot/windows-server/windows-security/restrict-cryptographic-algorithms-protocols-schannel.
There’s a free tool that you can use to sort out all of the above https://www.nartac.com/Products/IISCrypto