Hi,
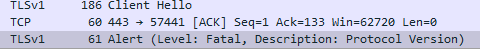
A connector that uses a HTTPS connection is failing the handshake between both entities (DataMiner and product) due to the TLS version (DataMiner is offering v1.0).
I’m also not sure whether the self-assigned certificate a negative impact on the communication (from postman we are able to connect when SSL verification is disabled). Do we need to install the self-assigned certificate under Trusted CA? It seems that from DataMiner v10.0.5 onwards we able to overcome this issue by adding the loginMethod to the session. Refer to the following RN: https://community.dataminer.services/documentation/dataminer-v10-0-5-release-notes/?hilite=%27client%27%2C%27certificate%27 . Could you confirm whether this option is indeed for such situations?
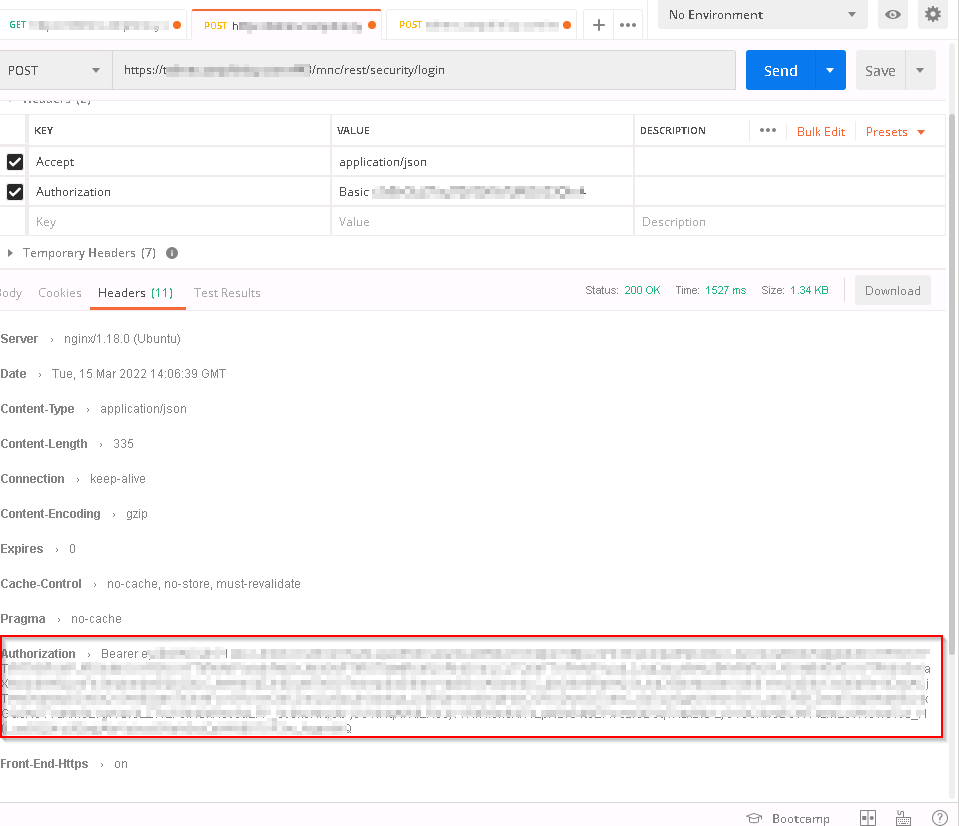
Also, this product mixes authentication methods, notably BASIC and BEARER. From what I could see, the bearer is retrieved from the response header. Will I be able to get such data from a QAction?
Kind regards,
Hi Flavio,
From the Wireshark capture, it looks like the TLS handshake is failing on the Protocol version, likely meaning the device is not accepting TLS v1.0. You can check which TLS versions the device/API is supporting by running a tool like SSL Scan. Could you verify which TLS versions your device allows?
Could you also share your DataMiner version?
Hi Jens,
Indeed, I’ve forgot to mention that. The device uses v1.2. Can we “force” DataMiner to use/request this version?
DataMiner version: 10.0.0.0-9962-CU11
Kind regards,
Hi Flavio,
Which version of windows server is installed on your servers?
Hi Ive,
The server is running Windows Server 2008 R2 Standard.
It is worth to mention that Postman calls from the same server are using TLS v1.2.
Kind regards,
Hi Flavio, could you try setting these WinHttp registry keys (see link below) on the server? This will change the default TLS versions used by clients (which DataMiner is in this case). From Windows Server 2012 (R2) onwards this is already the case.
Next to the registry keys I mentioned in the previous comment, you’ll probably also have to export the certificate from the web server and add it to the Trust Root Certificate Authorities in the Certificate Store of the DataMiner server. This guide explains how you can do this: https://techcommunity.microsoft.com/t5/windows-server-essentials-and/installing-a-self-signed-certificate-as-a-trusted-root-ca-in/ba-p/396105
Would “Headers” tag under the “Response” do the job for retrieving the Authorization bearer?