Hi Dojo,
I have local DMA and Cassandra that gets installed by DMA installer 10.2. My DMA version is 10.4.6. I would like to update my Cassandra to newer version, ideally I would remove Cassandra completely and install new version. I don’t care about any data in the DB but I’m not sure if DMA will care or if I can just point it to the new Cassandra and it will automatically setup everything it needs on the new DB.
Where can I find information about supported Cassandra versions?
I’ve also been trying to setup Cassandra to use TLS and generating certificates with the script that is mentioned in the DataMiner docs however that script doesn’t seem to work. It does generate certificates but Cassandra refuses to run with them. Is generate-tls-certificates repo still up to date and useable?
I also had issues with “curl https://localhost:9042” where it returns HTTP0.9. Is this expected response from Cassandra or is it an issue with my cassandra.ymal configuration?
Thanks
Hi Bert,
Thanks for the tip, but since I’m using it for experimenting and playing around I would like to avoid incurring additional cost for those purposes.
Cheers
Hi,
Depending on where you have the Cassandra instance installed, different versions can be used. If you are running Cassandra on Windows, it’s not possible to update to Cassandra 4.0 or newer. If you are running Cassandra on Linux, you should be able to update to any version withing the 4.x range.
For the TLS, the script should still be working and is actively maintained. Can you please share the errors you get when using certificates generated by the script?
Kr,
I was thinking about installing Docker and running Cassandra 4 on it, would that work? How big of performance hit would it be?
Not sure about Docker but you could try to use WSL to run cassandra.
However, if I were you I would start looking at STaaS, especially if it’s only for some experimenting. The time spent setting up and maintaining Cassandra will far outweigh the small cost of using STaaS.
Hi Seppe,
Thank you for your patience and assistance. I’ve decided to move to STaaS and I must say I’m impressed how fast and easy it was, especially considering I’ve spent at least 40 hours trying to setup TLS on both Cassandra and Opensearch since your BPA Kata. In contrast, STaaS took about 5 minutes. At least I learned a lot… #copium
Hi Seppe,
I get following exception in Cassandra logs on startup:
ObjectIdentifier() — data isn’t an object ID (tag = 48).
I’m using keytool from C:\Program Files\Java\jdk-22\bin. I tried with keytool from C:\Program Files\Java\jre-1.8\bin with same results.
I’ve also tried both keytools with store_type: JKS in which case I get Invalid keystore format, which makes sense for jdk-22 since it does say it created PKCS12 store, but when I use script with jre-1.8 I can see warning about using JKS store and still the store apparently ends up being of type PKCS12.
I tried commenting out protocol, algorithm, store_type and cipher_suites for both server and client encryption with no avail.
This is my cassandra.yaml:
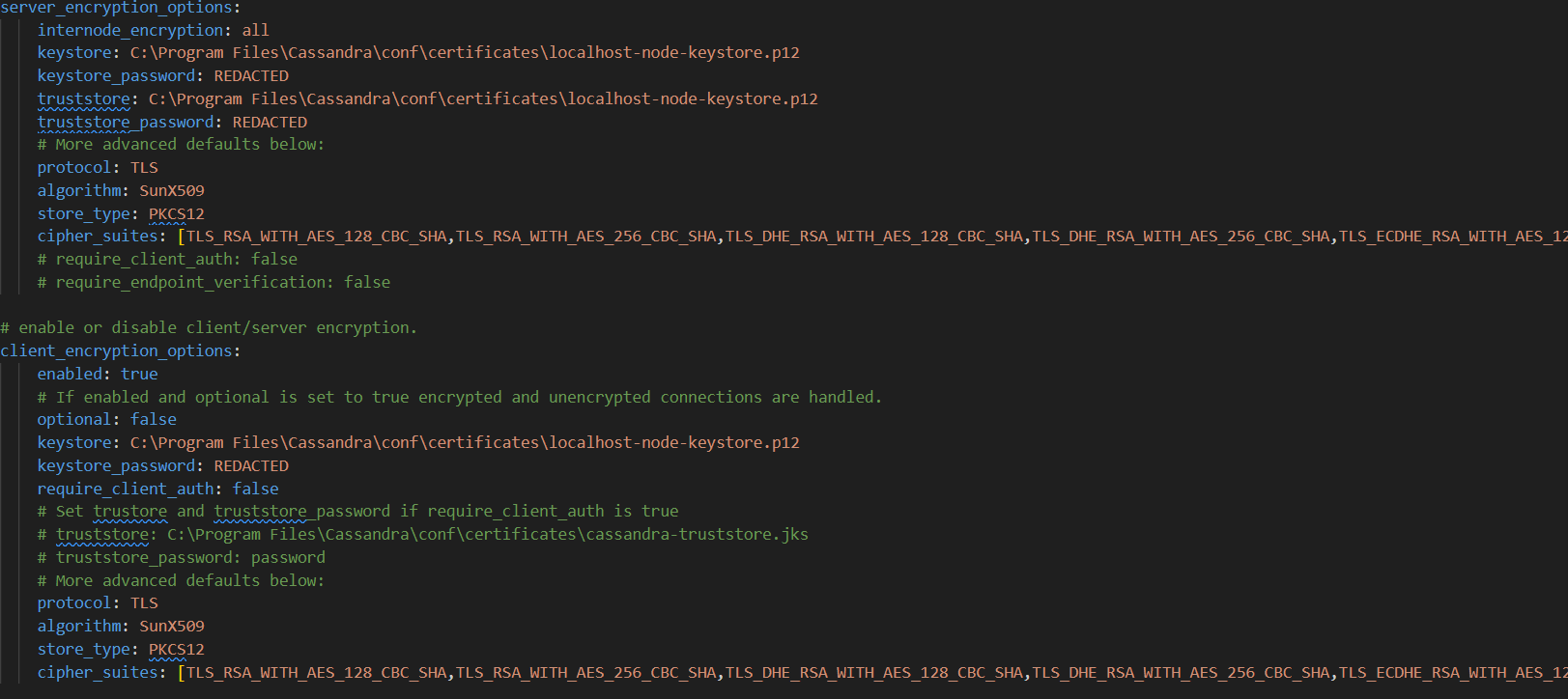
Full list of cipher_suites:[
TLS_RSA_WITH_AES_128_CBC_SHA,
TLS_RSA_WITH_AES_256_CBC_SHA,
TLS_DHE_RSA_WITH_AES_128_CBC_SHA,
TLS_DHE_RSA_WITH_AES_256_CBC_SHA, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA, TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA]
As far as I could figure ObjectIdentifier() — data isn’t an object ID (tag = 48) exception is related to JVM version, but since I’m using the newest one I’m not sure what else could be the cause and that’s why I was thinking updating Cassandra would fix it. I also tried setting JAVA_HOME environment to point to both jre-1.8 and jdk-22 with same results.
Hi,
My first guess is that the encryption algorithm used to encrypt the PCKS12 file is not (yet) supported by Java. To test this, I would to check which openssl and java versions that were used for the generation of the certificates, and which java version that is used by cassandra.
“AES encryption in pkcs12 is not supported in java up to java 11” and cassandra 3.x uses Java 8. How hard would it be to modify the script to not generate AES keys? Do you think that’s something I could do myself?
I would assume that you have openssl 3.x installed, while the script was developed and tested using the openssl 1.x range. You could try to solve this by adding the ‘-legacy’ option to the openssl operations in the script.
FYI: it’s now recommended to use STaaS, this will immediately solve all your questions here and you’ll have more time and more compute resources again to focus on other things.