I have a chassis that can spin up Firewall Applications on the fly. The chassis has 2 ethernet ports that must be connected to the network switches. For the other traffic the user has to insert some ethernet modules.
To make this setup as generic as possible I want to make use of just one Firewall Service Definition instead of one for source and one for destination.
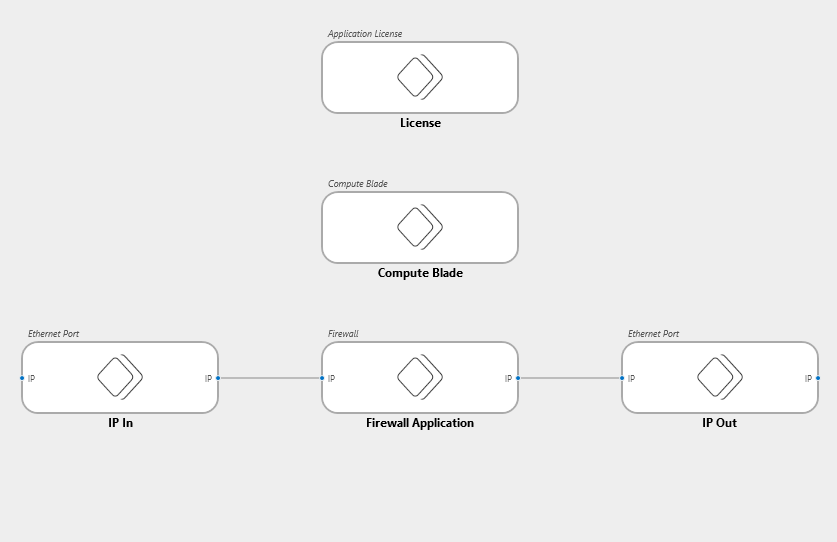
Based on where the edge device is located in the signal flow (source or destination) the chassis ethernet port resources will get assigned to IP Out (source) or IP In (destination).
To make a distinguish between the chassis ethernet ports I've added a Ethernet Port_Network Connected capability to the resources.
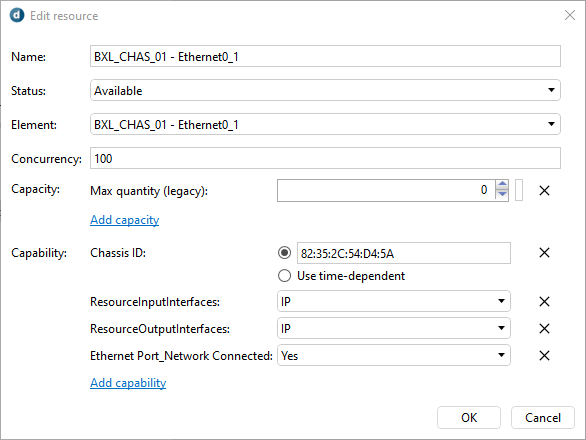
I'm looking for a way that the user can select in the Booking Wizard if the edge device will be used as Source or Destination and based on the value will configure the Ethernet Port_Network Connected capability.
I saw users using the the Resource Assignment property on a node, but I couldn't find documentation about it. I also don't know how far this feature can do what I want to achieve?
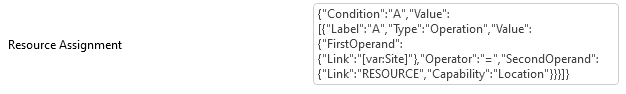
The Resource Assignment property on the node of a service definition allows you to ask the user in the booking wizard to select a specific resource capability to be present before going to the resource assignment page. This is typically done for capabilities which do not fit into a profile definition. (such as location)
An example, which is also your example in the resource assignment string above, is having resources on many locations, tagged with a specific Location capability.
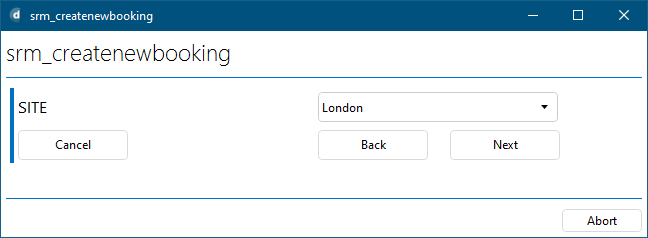
With your resource assignment configuration, the booking wizard will retrieve the various available resources for a specific node, get the different Location capabilities, and present this as a drop-down to the user. The selection will of the capability will then automatically already reduce the resource selection to the chosen capability. In example below, will only result resources that are located in London.
Going back to your initial question, whether the firewall needs to act as input and/or output is an orchestration, I assume? In other words, firewall application are not limited by a certain input/output capability, but simply need to be configured that way?
It is indeed an orchestration and the application itself isn’t limited by input/output capabilities. In our design we decided that the 2 ethernet interfaces on the chassis must always be connected to the network switches. This means that when the firewall is used as a source edge device the chassis ethernet interfaces should only be selected as IP Out resources. Vice versa in case the firewall is used as destination edge device.