We face an issue with huge number of authentication failure logs generated from DataMiner and we know the reason: when a user account configured for monitoring a network device (Microsoft platform elements mainly) and at a point where the account is no longer authorized to access the element, yet remains in the element record, the element eventually gets into communication timeout state.
This event triggers continues logon attempt to this element which is an InfoSec concern.
When InfoSec reports this, and to update this kind of elements, we will have to go through each of them and see if the specified account is configured which is long process to go through.
Could you please explain how can we find a specific account configured to monitor any of the elements? Or maybe the elements from a specific DMA?
Hi Ciao,
One thing you could do, is use the multiple set feature in Cube. You right click on one of those elements using that protocol, Microsoft Platform in this case. Then you choose Multiple Set and you select the Username parameter. This will show all the elements using that protocol with their current value for this parameter.
Example:
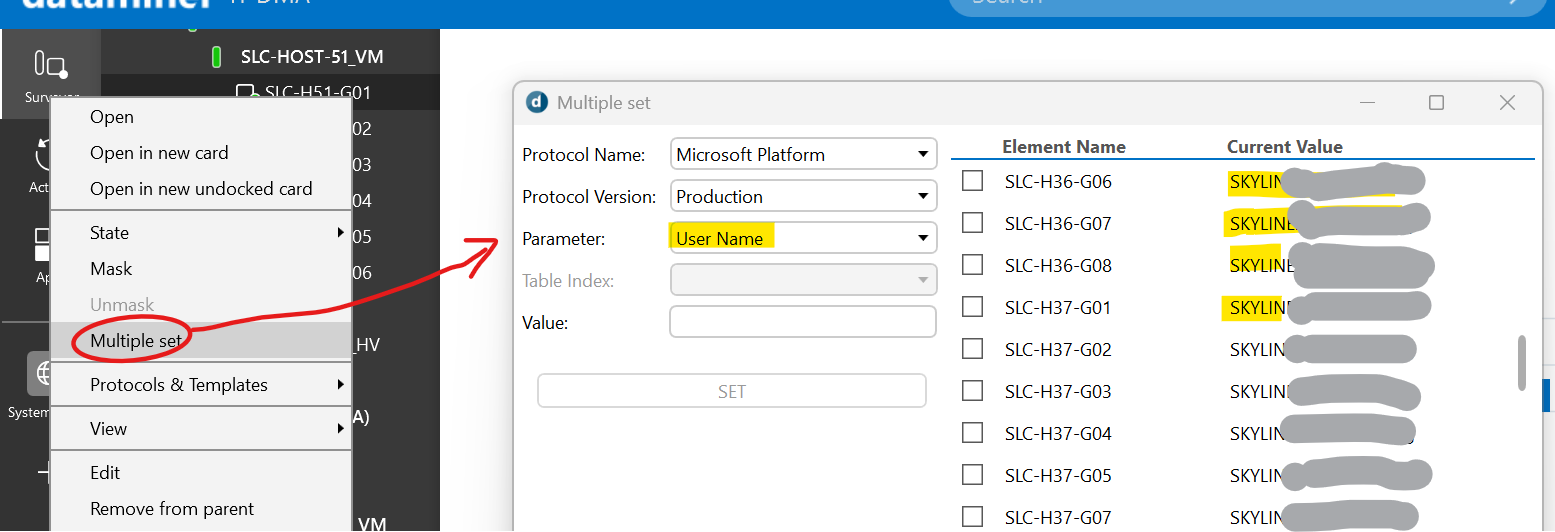
Probably you could also do something in dashboards, and you could also look at the timeout alarms, because all affected elements are in timeout...
Bert
Hi Caio,
Regarding the Microsoft Platform connector, please if you can create a task to further investigate this issue. I believe the connector should be able to handle this corner case.
We could also double check the slow polling settings, but I believe in this case it will not apply since the Windows host will still reply with 'access denied'.
The credentials are available in the page 'Performance' -> Page button 'Security'. If you would like to update the credentials on multiple elements, you could use the multiple set feature.
Hope it helps.