Good afternoon,
I’m writing to ask a question about the configuration of AWS credentials in a DataMiner agent running on a EC2 instance.
To give some context, we need to monitor AWS MediaConnect flows which are in a different AWS account as the one where the DataMiner EC2 instance is running.
It looks like we have 2 main options to specify AWS IAM credentials at the moment:
- Passing IAM User credentials (Access key and Secret Key) of a user which is defined in the same account of the MediaConnect flows I want to monitor: this solution force us to use long-lived credentials (not a best practice), and to implement rotation of these credentials.
- Passing the name of the DataMiner EC2 instance role, which stores the temporary credentials in the EC2 metadata. This assumes that the MediaConnect flows are defined in the same account where DataMiner EC2 is running, which is not the case for us.
I wanted to know whether it’s possible to configure the AWS MediaConnect connector to use a IAM role which is defined in a different account where the DataMiner EC2 is running on.
Also, any links to updated docs on this topic would be greatly appreciated – so far I have found this page, which seems outdated (it does not even mention the EC2 metadata option mentioned in point n.2 above).
Kind regards
Arunkrishna,
We have something similar in the AWS cloudwatch connector. Assuming it’s the same, we can extend this capability to the mediaconnect connector as well.
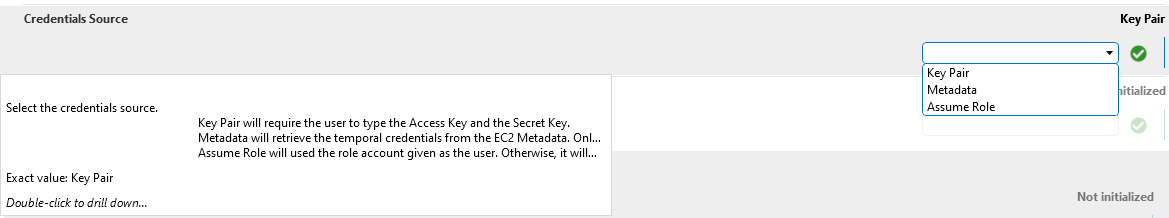
We will update the documentation for the connectors to show all authentication mechanisms.
Thanks.