In today’s digital landscape, properly securing your data and systems is of the utmost importance. To reduce security risks as much as possible, you should go beyond the out-of-the-box DataMiner configuration and take the steps outlined in our DataMiner hardening guide.
Keep your system up to date
Your first step should be to make sure your system is always up to date. This includes the operating system and all installed software. This way, you have access to the latest security fixes and features. To get the most recent version of DataMiner and related software, go to the Downloads page here on Dojo.
Use the available BPA tests
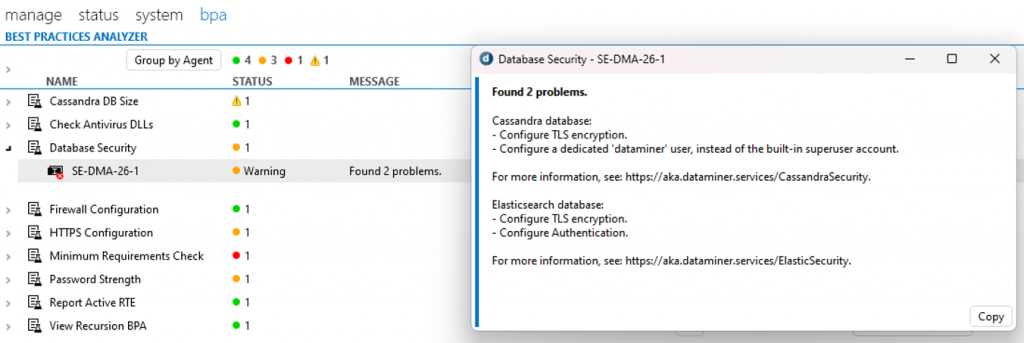
The next step to start hardening DataMiner is to make use of the available BPA tests. These scan your DataMiner System for all sorts of issues and will help you resolve any detected issues. For security, the Database Security, Firewall Configuration, and HTTPS Configuration tests are the most important. All three of these are available by default from DataMiner 10.2.12/10.3.0 onwards.
After you have run these BPA tests, they will provide an overview of the detected issues and point you to the right documentation to resolve them.
Switch to HTTPS
There are several changes you can implement to the default DataMiner configuration to harden the security of your system. The first is to switch to HTTPS. By default, DataMiner uses HTTP to serve its web applications, but this is unencrypted and vulnerable to man-in-the-middle attacks. Setting up HTTPS instead will close this door to possible attackers.
When you do so, we also recommend that you configure your operating system to block deprecated SSL/TLS versions. HTTPS uses SSL/TLS for encrypting communication, but the older versions of this protocol are no longer considered secure. At present, all major browsers support the latest TLS version (TLS 1.3), but TLS 1.2 is also still regarded as secure. All older versions are deprecated.
Switch to gRPC
The next change you can implement is to switch to gRPC for DataMiner client-server and server-server communication instead of the default .NET Remoting. By default, Cube uses .NET Remoting to communicate with DataMiner. From DataMiner 10.1.7 onwards, this communication is encrypted using the Rijndael algorithm using a 256-bit key, which is negotiated over a 1024-bit RSA encrypted communication channel. For the communication between DataMiner Agents in a cluster, .NET Remoting is also used by default.
However, .NET Remoting is a legacy technology and is no longer considered secure. This is why you can switch to a gRPC connection from DataMiner 10.3.2 and 10.3.0 CU0 onwards, as a more secure alternative. You can configure this in ConnectionSettings.txt for the client-server communication and in DMS.xml for the server-server communication. Note that this is still a beta feature in DataMiner 10.3.2 and 10.3.0 CU0, so you may still encounter issues and the connection might still be less stable than with .NET Remoting.
Configure your firewall
Depending on the version of the DataMiner installer you used, and depending on how you have configured your system, you may be able to close several ports and disable certain rules in the Windows firewall. For example, if you configured your DataMiner Agents to use gRPC for client-server communication and server-server communication, port 8004 can be closed. For gRPC communication, port 443 is used instead, which is also used for HTTPS. For a full overview of the ports you may be able to close, refer to the DataMiner hardening guide.
Secure the databases
Cassandra and Elasticsearch are a crucial part of recent DataMiner Systems. For this reason, it is important that you spend some time making sure the configuration of these databases is as secure as possible. For detailed information, see Securing self-managed DataMiner storage.
Check out our DataMiner hardening guide
Did you spot several things in this blog post that could also be improved in your DataMiner System? Go take a look at our detailed DataMiner hardening guide, and follow the different steps we explain in it to make your system as secure as possible.
Great article, Seppe!
Wow, this is amazing.
Great summary overview!
Great article thanks for sharing