Hi all,
I’m creating a protocol to fetch DHCP information through powershell.
I’m able to access the information if I:
- Open a powershell instance;
- run start powershell -credential “”
- introduce username and password of another user with permissions to access such information
- run Get-DhcpServerv4Scope -ComputerName “swic3dhcp1”
Without step 2 I’m not able to run step 4, due to lack of permissions.
After doing some investigation, the only way I was able to successfully launch a powershell instance with permissions to fetch the DHCP data was by using ‘SimpleImpersonation‘ NuGet, that uses the LogonUser Windows API to run code as another user:
using (SafeAccessTokenHandle userHandle = credentials.LogonUser(LogonType.Interactive))
{
response = WindowsIdentity.RunImpersonated(userHandle, () =>
{
var ps = PowerShell.Create();
ps.AddScript(@”Get-DhcpServerv4Scope -ComputerName “”swic3dhcp1″””);
return InvokeSafe(ps, protocol);
});
}
However, once the LDAP Resync task runs a lot of users belonging to a group are removed from DataMiner and it’s no longer possible to access the Agent with those accounts:
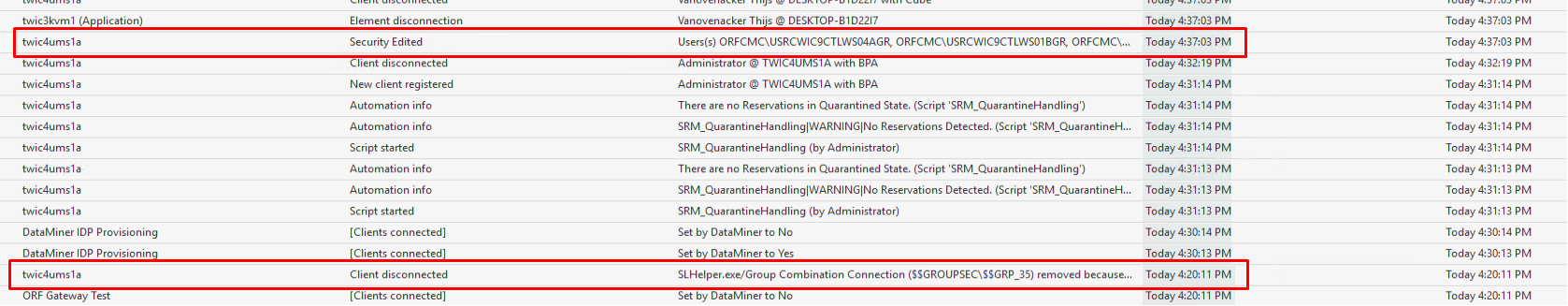
Text of the highlighted events:
‘twic4ums1a’ | ‘Security Edited’| ‘Users(s) ORFCMC\USRCWIC9CTLWS04AGR, ORFCMC\USRCWIC9CTLWS01BGR, ORFCMC\USRCWIC9CTLWS01AGR, ORFCMC\USRCWIC9CTLWS03AGR, ORFCMC\USRCWIC9CTLWS03BGR, ORFCMC\USRCWIC9CTLWS02BGR removed from group ORFCMC\res.adm25.svcDataminer.CMC.Playout By DMS-synchronization from Active directory’
– Today 4:37:03 PM
‘twic4ums1a’ | ‘Client disconnected’ | ‘SLHelper.exe/Group Combination Connection ($$GROUPSEC\$$GRP_35) removed because of error: Unable to connect to the remote server’
-Today 4:20:11 PM
NOTE: I also checked how powershell commands are executed in the node tool automation script and I get an exception: access is denied when creating a PSSession object.
Given that I’m using WindowsIdentity.RunImpersonated, contained in the System.Security.Principal namespace, I believe using this is messing up something in the Active Directory.
If I cannot use this approach, can somebody suggest how to get around this?
Thanks in advance.
Best Regards
Yes, they only get removed in the synchronization after the code runs. If I restore the security.xml file and don’t run that piece of code, the synchronization will not remove any account.
I have had success in the past with running methods as an impersonated user by following the example given on this page:
WindowsIdentity.Impersonate Method (System.Security.Principal) | Microsoft Docs
It looks similar to the code the NuGet you are using implements but I do not use the RunImpersonated call.
Instead, like in the example, I call WindowsIdentity.Impersonate and after that, I just run my normal methods as if no impersonation was needed.
I’ve used WindowsIdentity.Impersonate and it works perfectly without removing DataMiner users.
Looks like this solves the impersonation issue.
Thanks for the help!
Are the users still part of the group on the DC / Active Directory?