We are trying to connect our newly installed DataMiner cluster (1 pair of DMAs) to our Amazon Keyspace and OpenSearch DBs. We followed the steps from https://docs.dataminer.services/user-guide/Advanced_Functionality/Databases/Database_configuration_in_Cube/Configuring_the_database_settings_in_Cube.html#amazon-keyspaces. However, we have a question about credentials we need to provide for the Keyspaces configuration.
The instructions tell us to provide the following:
- DB Server: The URL of the global endpoint of the region your Amazon Keyspaces cluster is in. (e.g.
cassandra.eu-north-1.amazonaws.com).
Our region is EU-West-2, so we entered “cassandra.eu-west-2.amazonaws.com”. - User: The username of your AWS user account.
We created a special IAM user and gave it access to AWS Console and Keyspace - Password: The password of your AWS user account.
We provided the AWS Console password
Our question is about the username and password.
- How would DM know which AWS accuont ID that user belongs to?
- Can we provide an access token instead of the password?
- Do we need to create a keyspace and attach it to the config?
Currently, we are getting the following exception complaining about the credentials
2023/03/30 06:30:48.540|SLDBConnection|CertificateValidationCallback|INF|0|51|Certificate for subject ‘cassandra.eu-west-2.amazonaws.com’ (issued by CN=Amazon RSA 2048 M01, O=Amazon, C=US) is valid (from 03/14/2023 00:00:00 to 03/13/2024 23:59:59
2023/03/30 06:30:48.550|SLDBConnection|CassandraConnection::Connect|ERR|0|1|Cassandra.NoHostAvailableException: All hosts tried for query failed (tried 3.10.201.205:9142: AuthenticationException ‘Provided username ************** and/or password are incorrect’)
at Cassandra.ControlConnection.<Connect>d__31.MoveNext()
— End of stack trace from previous location where exception was thrown —
at System.Runtime.ExceptionServices.ExceptionDispatchInfo.Throw()
at System.Runtime.CompilerServices.TaskAwaiter.HandleNonSuccessAndDebuggerNotification(Task task)
at Cassandra.ControlConnection.<Init>d__30.MoveNext()
— End of stack trace from previous location where exception was thrown —
at System.Runtime.ExceptionServices.ExceptionDispatchInfo.Throw()
at System.Runtime.CompilerServices.TaskAwaiter.HandleNonSuccessAndDebuggerNotification(Task task)
at Cassandra.Tasks.TaskHelper.<WaitToCompleteAsync>d__8.MoveNext()
— End of stack trace from previous location where exception was thrown —
at System.Runtime.ExceptionServices.ExceptionDispatchInfo.Throw()
at System.Runtime.CompilerServices.TaskAwaiter.HandleNonSuccessAndDebuggerNotification(Task task)
at Cassandra.Cluster.<Init>d__36.MoveNext()
— End of stack trace from previous location where exception was thrown —
at System.Runtime.ExceptionServices.ExceptionDispatchInfo.Throw()
at System.Runtime.CompilerServices.TaskAwaiter.HandleNonSuccessAndDebuggerNotification(Task task)
at Cassandra.Cluster.<ConnectAsync>d__44`1.MoveNext()
— End of stack trace from previous location where exception was thrown —
at System.Runtime.ExceptionServices.ExceptionDispatchInfo.Throw()
at System.Runtime.CompilerServices.TaskAwaiter.HandleNonSuccessAndDebuggerNotification(Task task)
at Cassandra.Cluster.<ConnectAsync>d__43.MoveNext()
— End of stack trace from previous location where exception was thrown —
at System.Runtime.ExceptionServices.ExceptionDispatchInfo.Throw()
at Cassandra.Tasks.TaskHelper.WaitToComplete(Task task, Int32 timeout)
at Cassandra.Cluster.ConnectAndCreateDefaultKeyspaceIfNotExists(Dictionary`2 replication, Boolean durableWrites)
at SLCassandraClassLibrary.DBGateway.Cassandra.StorageManagers.SingleNode.CassandraConnection.Connect(Boolean createDefaultKeyspace)
2023/03/30 06:31:18.552|SLDBConnection|CassandraConnection::Connect|INF|0|1|Reconnecting… (attempt #46)
Thanks
Hi Saddam,
Apologies for the confusing, but the regular AWS credentials won’t work indeed.
In the Identity and Access Management (IAM) Service you can generate new credentials that are used to access the Amazon Keyspaces service. Those credentials are then linked to the account that created them.
In order to do this the right permissions are required.
All of this takes place in the IAM service.
- Go to IAM > Users
- Search for the account that should have access
- Verify this account has the permissions to generate Amazon Keyspaces credentials
- Then to generate credentials, go to the ‘Security credentials’ tab
- Scroll down to the Amazon Keyspaces part
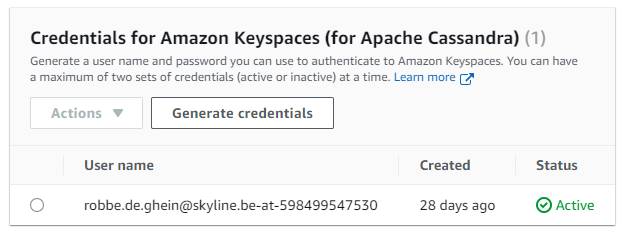
- Here you can generate up to 2 sets of Username-Password credentials at a time, which can be deactivated or deleted at any time, separate from your AWS account.
Hope this helps, if you have more questions, don’t hesitate to ask.
I’ll also update the documentation to make this more clear.
Kind regards.
Yes, will do!
Hi Saddam,
Thank you for your message
You did indeed correct to create an IAM user with AmazonKeySpace permissions. However, an additional step is needed. When this permissions are assigned, you have to go to “Security credentials” or that IAM user and then scroll down to “Credentials for Amazon Keyspaces”. There you can create new credentials.
The credentials that are created should then be used for the authentication in DataMiner.
AWS then knows that these credentials are connected to that AWS IAM user.
It’s not possible to use an access token as this is not generated. You have to use the username/ password combination.
Hope this resolved your question. In case you have some additional questions, don’t hesitate to reply.
Kind regards,
Thibault
Thanks a lot Robbe,
Could we add the steps you mentioned to the instructions as well please?