Hi all,
We are testing the driver Linux Platform 2.0.0.3 (this is the SNMP+SSH driver) on two different machines: one running OpenSSH 7 and another running OpenSSH 8.
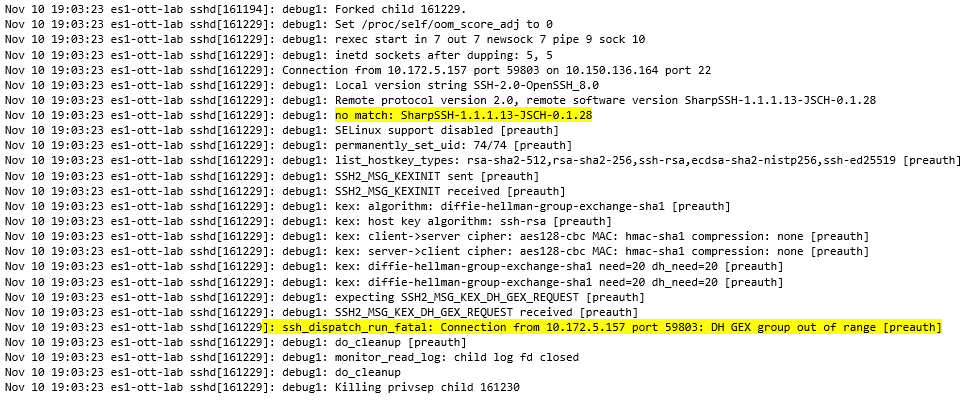
On the first one all works well, no issues there. On the second one the connections fails and we can see the following messages:
Is there any configuration that we are missing? Or does the driver require an update?
Thank you for your help.
With each new version of OpenSSH, they typically disable by default some key-exchange algorithms that are proven in the field to be less secure, some can be enabled again by the sysadmin, others are completely removed.
Within DataMiner we offer the following key-exchange algorithms to the SSH server in that order:
- diffie-hellman-group1-sha1
- diffie-hellman-group-exchange-sha1 (with maximum modulus size of 1024 bits)
- diffie-hellman-group14-sha1
- ecdh-sha2-nistp256
Judging from the logging that you posted, I believe they will have increased the minimum modulus size to > 1024 bits compared to the other version that you were testing against. To be able to setup connection successfully, you'll have to reconfigure the default order (defined in the software) from in the protocol. This can be done by setting the following on the connection:
<Connection id="1" name="SSH Connection">
<Type>serial</Type>
<CommunicationOptions>
<KexAlgorithms>
<KexAlgorithm>ecdh-sha2-nistp256</KexAlgorithm>
<KexAlgorithm>diffie-hellman-group14-sha1</KexAlgorithm>
<KexAlgorithm>diffie-hellman-group-exchange-sha1</KexAlgorithm>
<KexAlgorithm>diffie-hellman-group1-sha1</KexAlgorithm>
</KexAlgorithms>
</CommunicationOptions>
</Connection>
Which will result in preferring ecdh-sha2-nistp256 and diffie-hellman-group14-sha1 over the other two.
Thank you Jeroen, I was not aware of this detail, this was really helpful.